In this article, we’ll delve into TCP SYN Flood attacks, how they work, and how to perform and detect them using Wireshark.
A SYN flood attack is a type of Denial-of-Service (DoS) attack that exploits the TCP three-way handshake. By sending an overwhelming number of SYN packets to a server, attackers exhaust the server’s resources, leading to network congestion or making the server unavailable to legitimate users.
How Do SYN Flood Attacks Work?
To understand a SYN flood attack, let’s first review the normal behavior of the TCP three-way handshake, which establishes a reliable connection between a client and a server.
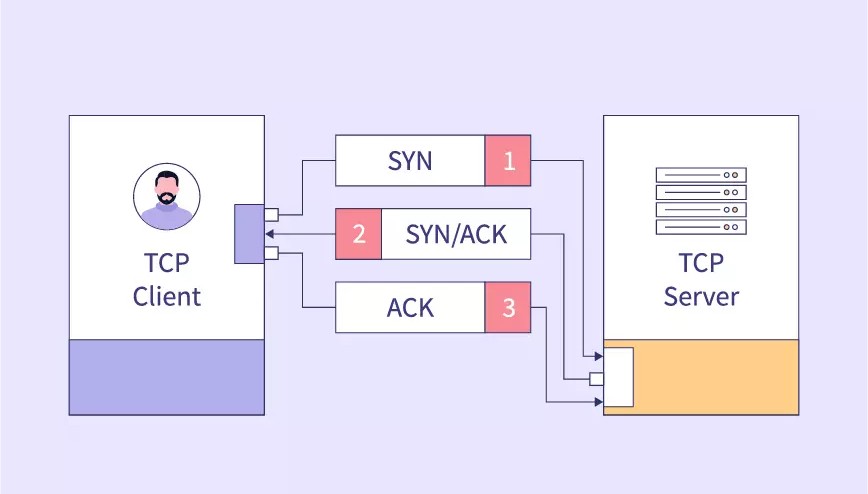
The TCP Three-Way Handshake
When a client initiates a connection with a server using the TCP protocol, the following steps occur:
- SYN (synchronize): The client sends a SYN packet to request a connection.
- SYN-ACK (synchronize-acknowledge): The server acknowledges the request by responding with a SYN-ACK packet.
- ACK (acknowledge): The client confirms the connection by sending an ACK packet back to the server.
Once this handshake is complete, the connection is established, and data can flow between the client and the server.
What Happens During a SYN Flood Attack?
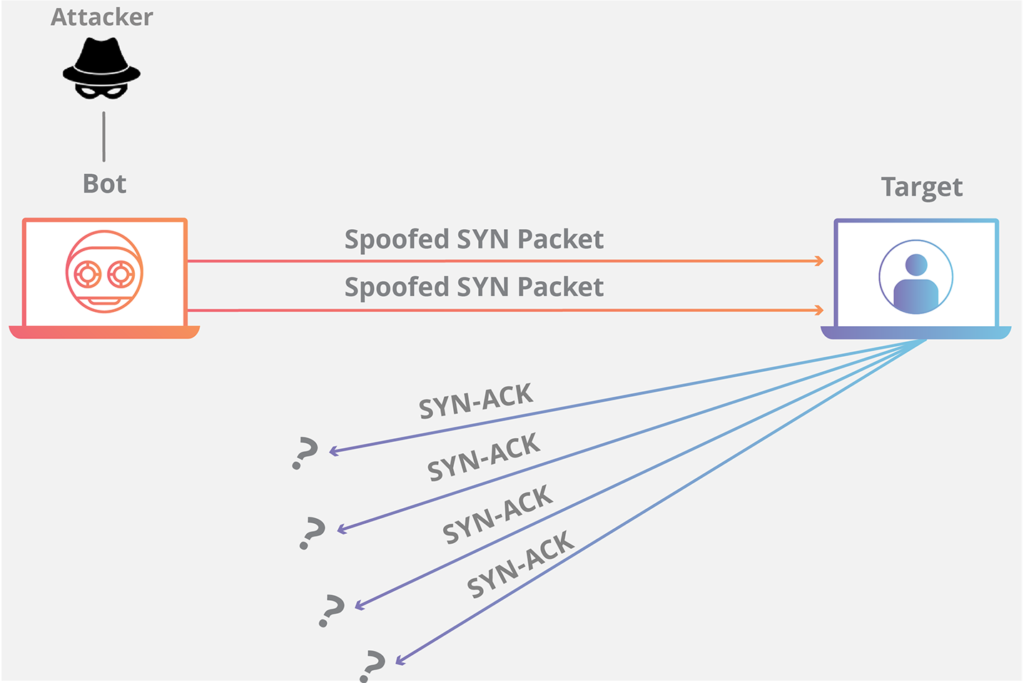
In a SYN flood attack, attackers exploit this handshake process by:
- Sending a massive number of SYN packets to the target server.
- Never complete the handshake by sending the corresponding ACK packets.
- Leaving the server waiting for acknowledgments, causing it to allocate resources for each incomplete connection.
Over time, these half-open connections consume the server’s resources, rendering it unable to handle legitimate traffic, resulting in a Denial of Service (DoS).
